Theme Context - Copy this React, Tailwind Component to your project
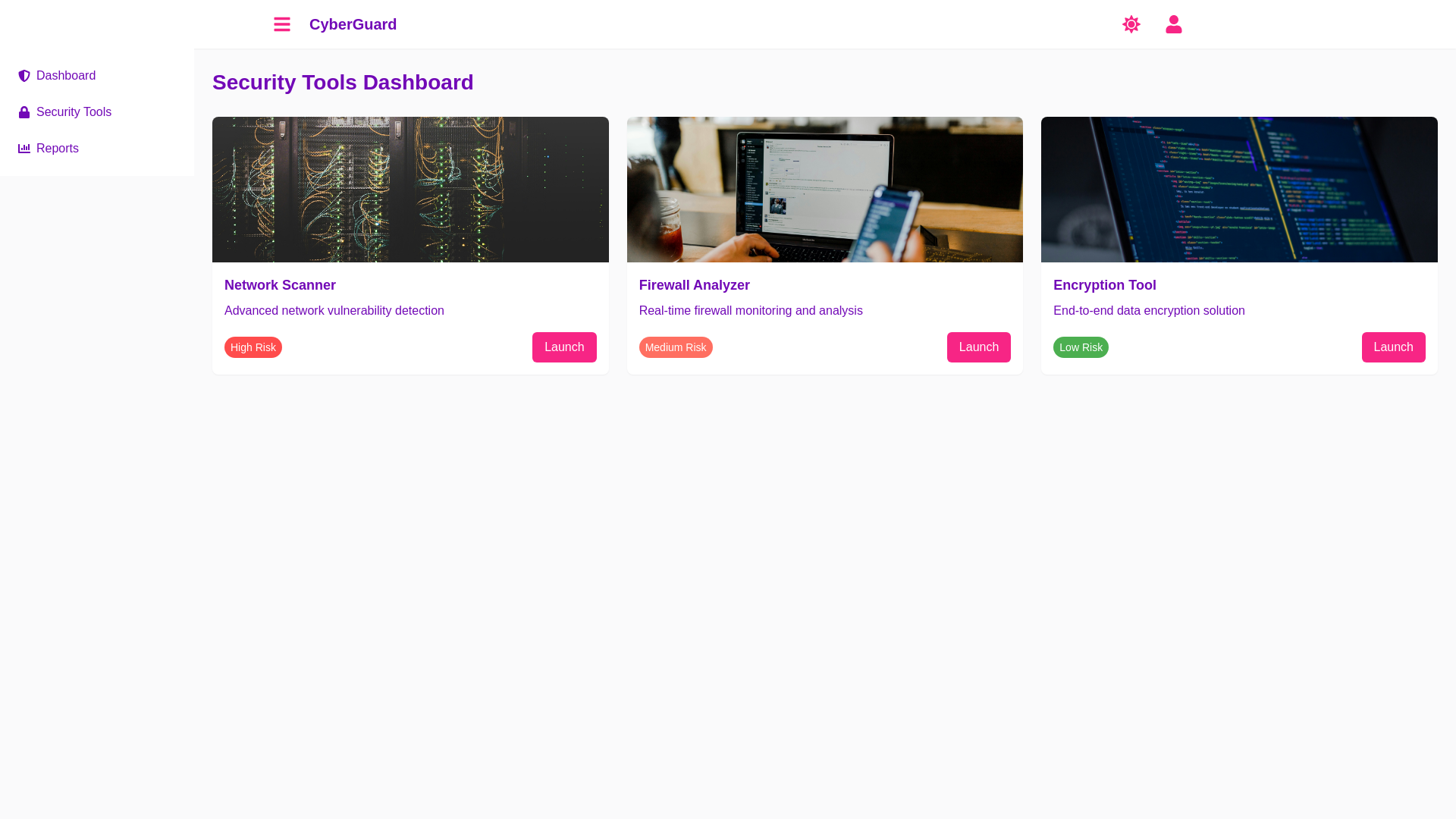
Decoding Cyber Vulnerabilities: Unleashing the Power of Top Security Testing Tools 1. Home Page (Landing Page) Design: Layout: A sleek, professional, and tech centric design focused on cybersecurity, with visual elements such as shield icons, locks, and code snippets, creating an atmosphere of trust and security. oHero Section: The homepage introduces the importance of identifying and decoding cyber vulnerabilities. A bold tagline like “Unleashing the Power of Security Testing Tools” will catch the attention of users. oIntroductory Banner: The project’s goals are highlighted with icons representing different tools and methods used for cybersecurity testing (e.g., penetration testing, vulnerability scanning). oColor Scheme: A dark color palette (blues, blacks) with accent colors like green or orange, which are often associated with security and alerts. Functionalities: Project Overview: Briefly describe how this platform decodes cybersecurity vulnerabilities using top security testing tools and techniques. Tool Showcase: Interactive tiles or a carousel showcasing popular security tools (e.g., OWASP ZAP, Nessus, Burp Suite). Navigation: Clear navigation links for sections such as Vulnerability Scanning, Penetration Testing, Report Generation, and Recommendations. User Experience: First Impressions: Users will immediately understand the focus on cyber vulnerabilities and security testing tools. Clear Navigation: The top navigation bar makes it easy for users to explore detailed sections about the tools, testing techniques, and reports. Appealing Design: The use of imagery, tool icons, and technical elements ensures the site feels professional and reliable. 2. Vulnerability Scanning Page Design: Layout: A structured page with sections explaining different types of vulnerabilities and the tools used to detect them. This page should emphasize scanning capabilities. oVisual Indicators: Scanning icons, progress bars, and vulnerability heat maps are used to represent the scanning process. oTool Demos: Live demonstrations of popular vulnerability scanners (e.g., OpenVAS, Nessus) could be embedded for users to interact with. Functionalities: Scan Tool Integration: Allow users to run vulnerability scans directly from the platform by inputting a website or IP address. Report Generation: Automatically generate reports based on the scans, listing the detected vulnerabilities, severity levels, and recommended actions. Scanning Options: Users can choose between different scanning levels (Quick Scan, Full Scan, Custom Scan). User Experience: Interactive Scanning: Users can directly engage with the tool by entering URLs or IPs to initiate scans. Easy to understand Reports: After a scan is complete, results are displayed in an intuitive and digestible format with color coded severity indicators. Scalability: Non technical users can run simple scans, while technical users can perform more detailed, customized scans. 3. Penetration Testing Page Design: Layout: This page will highlight the penetration testing process with visuals such as code injection, network penetration, and system breaches. oFlowchart of Penetration Testing: A flowchart or infographic explaining the stages of penetration testing—reconnaissance, exploitation, post exploitation, and reporting. oInteractive Elements: A demo section showing simulated attacks on a sample system or website to demonstrate how penetration testing tools like Burp Suite or Metasploit work. Functionalities: Penetration Testing Tools: Users can select penetration testing tools (e.g., Burp Suite, Metasploit, Wireshark) from a dropdown and initiate attacks on sample systems or applications. Live Attack Simulation: Simulate real world attacks in a controlled environment, allowing users to see how vulnerabilities are exploited. Test Reports: Generated test results will include attack success rates, exploitability, and the impact of attacks on systems. User Experience: Actionable Insights: Users can simulate attacks and see the real time impact, helping them understand potential risks in a safe, interactive environment. Step by Step Guidance: A simple, easy to follow guide will walk users through the process of performing penetration tests, with no prior experience required. Learning Platform: For beginners, a walkthrough of the testing steps and potential outcomes makes this educational as well as functional. 4. Security Tool Comparison and Features Page Design: Layout: A side by side comparison table showing the features, pros, and cons of top security testing tools such as OWASP ZAP, Burp Suite, Nessus, and Qualys. oVisual Aids: Icons and screenshots of each tool with a brief description of what they do. oCategory Filters: Users can filter tools by categories like Vulnerability Scanners, Penetration Testing, and Network Security. Functionalities: Tool Comparison: Allow users to compare key features and functionalities of different security testing tools in real time. Pros and Cons List: Display key differences in terms of ease of use, effectiveness, and pricing. Downloadable Resources: Provide links to download trials or documentation for each tool for users to explore further. User Experience: Quick Comparisons: Easy to read tables and visual aids enable users to quickly compare the tools and select the one that best suits their needs. Informed Decision Making: Users can make informed decisions about which security tool to integrate into their workflow based on a detailed analysis of features and capabilities. 5. Security Testing Reports Page Design: Layout: A clean design with sections that allow users to view detailed security testing reports. These reports will have a professional format similar to real world audit reports, including vulnerability descriptions, impact analysis, and remediation steps. oVisual Representations: Include charts, graphs, and tables summarizing vulnerability data, severity levels, and suggested actions. Functionalities: Custom Report Generation: Users can generate custom reports based on vulnerability scans and penetration tests. These reports can be downloaded in PDF or CSV format. Severity Levels: Vulnerabilities are categorized into severity levels (Low, Medium, High, Critical) and color coded for clarity. Suggested Fixes: For each vulnerability, the system will suggest actionable steps for remediation, such as applying patches, changing configurations, or improving security protocols. User Experience: In depth Reports: Security teams can use these detailed reports to address vulnerabilities. Actionable Remediation Steps: Clear, concise steps that users can follow to fix vulnerabilities, making the platform not just about identifying issues but also solving them. Professional Appearance: Reports will look polished and professional, suitable for presenting to clients or stakeholders. 6. Security Recommendations and Best Practices Page Design: Layout: Organized sections listing best practices for securing web applications, networks, and IT infrastructures. This page can be styled with infographics, checklists, and actionable guidelines. oStep by Step Security Plan: A well structured security plan that outlines how to improve security in stages. Functionalities: Best Practices Checklist: A checklist of recommended security measures, from basic password policies to advanced encryption methods. Actionable Guides: Each recommendation comes with a guide on how to implement it, whether it's configuring firewalls, updating software, or conducting regular security audits. Community Contributions: Allow users to contribute their own security practices or suggestions to build a community driven knowledge base. User Experience: Educational Resources: Users learn how to keep their systems secure through practical advice and step by step guides. Dynamic Updates: As new security vulnerabilities and solutions emerge, the recommendations will be updated, ensuring that users always have access to the latest security best practices. 7. General Features Across All Pages Design: Responsive Layout: The platform will be mobile friendly, ensuring that users can access security testing features on any device. Sleek Design: A modern, tech savvy design with clean lines, clear typography, and intuitive navigation. Functionalities: User Authentication: Allow users to log in, save testing results, and access customized reports. Tool Integration: Integrate popular security testing tools directly into the platform, so users can conduct testing without leaving the site. Real time Feedback: As users interact with tools, they will receive real time feedback on the success of their tests or the severity of identified vulnerabilities. Help Section: Detailed FAQs, troubleshooting guides, and live support chat for users who need assistance. User Experience: Seamless Interaction: Users can access all the security testing tools and features without complicated setup procedures or confusion. Comprehensive Tools: The platform ensures that both novice users and seasoned cybersecurity professionals can find value, with both beginner friendly guides and advanced features. Summary The Decoding Cyber Vulnerabilities: Unleashing the Power of Top Security Testing Tools platform provides a comprehensive, interactive solution for identifying, testing, and securing systems from vulnerabilities. With features like vulnerability scanning, penetration testing, security tool comparison, and customized reports, users are empowered to strengthen their cybersecurity posture using industry leading tools. Whether for businesses or individuals, this platform offers a user friendly and professional interface that makes complex security testing accessible to all levels of users.